Many of today’s most damaging scams are built on repeatable, well-understood patterns. The legal world defines four core elements of fraud with direct applicability to today’s phishing, impersonation, and account takeover (ATO) threats:
- False representation
- Knowledge of falsity
- Intent to induce reliance
- Reliance and resulting harm
By understanding this structure, security leaders and fraud teams can spot threats earlier and counter them more effectively. In this blog, we’ll explore each element using real-world examples from account takeover fraud and brand impersonation attacks, and show how businesses can stop fraud before it spreads.
What Are the 4 Elements of Fraud?
The classic legal framework for fraud includes:
False representation: A lie, misstatement, or deception presented as truth.
Knowledge of falsity: The fraudster knows it’s false and intends to deceive.
Intent to induce reliance: The falsehood is designed to manipulate a specific action.
Reliance and harm: The victim believes the falsehood, acts on it, and suffers damage.
In cyber fraud, these legal principles map cleanly to common scam patterns. A fake login page is a false representation. The attacker knows it’s a lie and intends to trick the victim into providing access credentials. This framework isn’t just academic, it helps security teams model threat behavior and improve incident response protocols.
Sidebar: While the legal model focuses on outcomes, the “fraud diamond” used in forensic accounting adds psychological factors, pressure, opportunity, rationalization, and capability.
How Each Element of Fraud Manifests in Cyberattacks
False representation can take the form of counterfeit websites, spoofed SMS messages, or lookalike social media profiles.
Knowledge of falsity is evident when attackers register typosquatted domains or cloak malicious content to avoid detection.
Intent to induce reliance appears in urgent phishing messages urging users to reset passwords, verify payments, or avoid account lockouts.
Reliance and harm follow when a user clicks a link, enters their credentials, or downloads a malicious file, leading to credential theft, financial loss, or data breaches.
This breakdown helps translate abstract legal terms into concrete digital indicators.
Real-World Example: How the 4 Elements Show Up in a Brand Impersonation Scam
Let’s say a scammer creates a lookalike website mimicking an airline. It’s convincing. Same fonts, same logo. Here’s how the elements map:
- False representation: The fake site pretends to be the real airline.
- Knowledge of falsity: The fraudster registers a lookalike domain and copies branding.
- Intent to induce reliance: Customers are tricked into entering booking details and card numbers.
- Reliance and harm: Victims lose money, and the real airline suffers reputational damage.
These scams often evade detection until after customer harm occurs, especially when they hijack SEO or run ads.

Real-World Example: Account Takeover via Phishing and MFA Bypass
Imagine this sequence:
- Victim receives a phishing SMS claiming to be their bank.
- Link leads to a fake login portal (looks legit).
- Victim enters credentials and unknowingly hands over MFA code.
- Attacker logs into the real account.
Fraud elements in play:
- False representation: The fake login page.
- Knowledge of falsity: The attacker mimics the bank on purpose.
- Intent to induce reliance: The message is designed to elicit trust and quick action.
Reliance and harm: The user is tricked and their account is compromised.
Most companies detect this only after fraud has occurred. That’s the gap Memcyco’s real-time phishing, ATO and digital impersonation platform closes.
Read more: Why top industry analyst, Datos Insights, featured Memcyco in its Q1 Fintech Spotlight 2025 Report.
What Most Businesses Miss About the 4 Elements of Fraud
Understanding fraud’s structure isn’t academic; it’s tactical. Modern scams exploit all four elements simultaneously. Digital impersonation attacks use visual deception. ATOs rely on misplaced trust. In fact, as cybersecurity analyst Ken Palla noted in his blog post “Disrupting AI-Powered Phishing: What CISOs Must Do Now”, organizations that fail to anticipate how AI is reshaping fraud vectors risk being permanently behind. His advice to CISOs (and downloadable capability maturity scorecard) emphasizes the need to act before phishing and impersonation attacks gain momentum.
Memcyco data shows a sharp rise in digital impersonation and ATO tactics that abuse user trust in brand identity, authentication, and digital familiarity. Delayed detection gives fraudsters more time to scale, automate, and monetize attacks.
Why Most Businesses Miss the Early Signals
Many businesses still rely on traditional detection tools that flag anomalies only after the fraud is complete. These tools often overlook:
- Subtle lookalike domains
- Unexpected device fingerprints
- Suspicious referral paths
By failing to recognize these early signals tied to the four elements of fraud, businesses leave themselves vulnerable to scalable, automated scams.
These blind spots aren’t limited to direct attacks. Fraudsters increasingly exploit partners and vendors as entry points. Third-party fraud introduces additional exposure, yet many organizations overlook it until the damage is done.
6 Practical Ways to Prevent Fraud Using What You’ve Learned
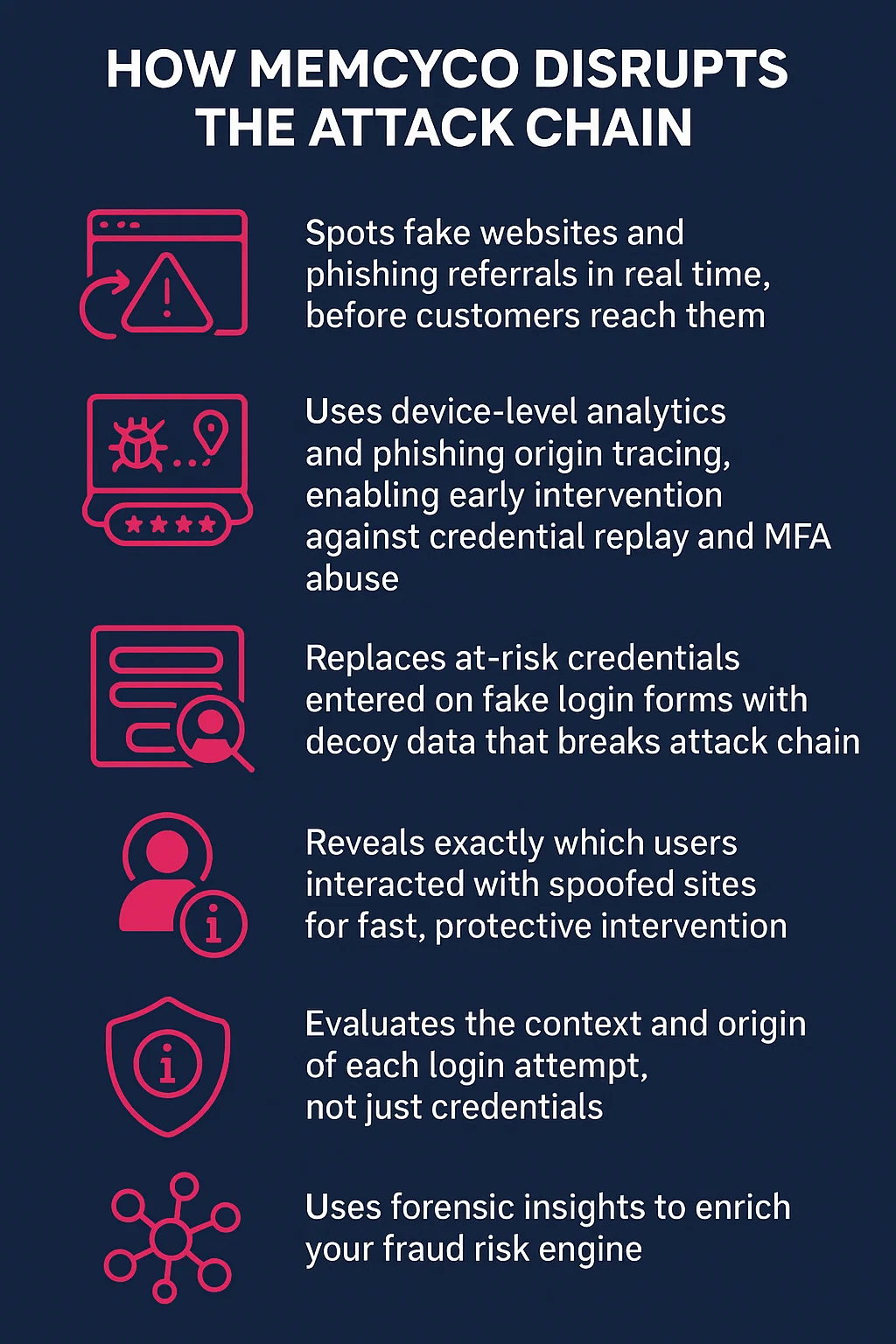
1. Detect impersonation before users are tricked
Memcyco spots fake websites and phishing referrals in real time, before customers reach them.
2. Lock out ATO attempts at first contact
Device-level analytics and phishing origin tracing enable early intervention against credential replay and MFA abuse.
3. Make fake sites and stolen credentials worthless
Stolen data is instantly replaced with decoy values that break attack chains.
4. Track which customers were scammed in real time
Memcyco reveals exactly which users interacted with spoofed sites so you can respond before harm spreads.
5. Don’t just verify logins, verify origins
Memcyco evaluates the context and origin of each login attempt, not just credentials.
6. Use forensic insights to enrich your fraud risk engine
Memcyco provides detailed device and referral-level data that feeds directly into fraud models, enhancing accuracy and responsiveness.
Each tactic corresponds to one or more fraud elements, preemptively disrupting the scam lifecycle.
FAQs About the 4 Elements of Fraud as Part of Modern Scams
What are the four elements of fraud?
False representation, knowledge of falsity, intent to induce reliance, and resulting harm.
How does account takeover fraud work?
Scammers phish users for credentials, bypass MFA, and gain access to accounts using trusted-looking methods.
How can businesses detect fraud before it happens?
Look for mismatched domains, unfamiliar devices, sudden spikes in behavior. Memcyco automates this process using real-time detection signals and device-level insights, helping fraud teams act before harm spreads.
What’s the best way to prevent fraud from phishing and impersonation scams?
The best approach is layered: detect fake sites early, lock out attackers at first contact, use decoy data to break the chain, and respond in real time.
Can you give an example of a brand impersonation scam?
A fake airline site that steals booking data while mimicking the official design. False representation, knowledge of falsity, intent to induce reliance, and resulting harm.
How can businesses detect fraud before it happens?
Look for mismatched domains, unfamiliar devices, sudden spikes in behavior, Memcyco automates this process using real-time detection signals and device-level insights, helping fraud teams act before harm spreads.
Can you give an example of a brand impersonation scam?
A fake airline site that steals booking data while mimicking the official design.
How does account takeover fraud work?
Scammers phish users for credentials, bypass MFA, and gain access to accounts using trusted-looking methods.
Final Thoughts: Understand the Structure. Break the Pattern.
Fraud is scripted. If you understand the playbook, you can break it. Recognizing its structure helps you stay ahead. The four elements of fraud may be old, but today’s attackers repackage them into scalable, digital-first threats.
Memcyco gives you real-time visibility and control, before impersonation scams reach your customers. Request a demo to see it in action.